Vulnerability
On 09/29/2018 during the 0DAYALLDAY Research Event, a vulnerability—CVE-2018-5560—was discovered in the Guardzilla Security Video System (Model GZ521W). The issue sits inside the firmware: hard-coded Amazon Simple Storage Service (S3) credentials bundled with the device.
In this post I highlight the portion of the work I focused on to show how straightforward these vulnerabilities are to spot with the right tools. For the full disclosure, read the complete report.
After collaborating with Nick McClendon and Andrew Mirghassemi—who provided a firmware dump and binaries—I opened the main executable in IDA Pro and started hunting for interesting strings. Almost immediately I noticed several entries surrounding s3.amazonaws.com.

Following the references confirmed my suspicion: the strings were exports named accessKey, secretAccessKey, hostname, and bucket—exactly how AWS S3 credentials are structured.
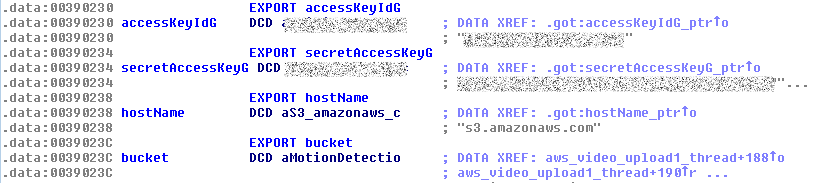
Chris later verified that these credentials had unrestricted access to every S3 bucket provisioned for that account.
Recommendations
- Stop using the Guardzilla GZ521W camera until a patch is released.
Disclosure Timeline
- Sat, Sep 29, 2018: Issue discovered at 0DayAllDay Research Event.
- Wed, Oct 3, 2018: Issue disclosed to Rapid7 for coordinated disclosure.
- Wed, Oct 24, 2018: Issue disclosed to vendor.
- Thu, Nov 8, 2018: Issue disclosed to CERT/CC as VRF#18-11-NPPXC.
- Fri, Dec 14, 2018: CVE-2018-5560 reserved.
- Thu, Dec 27, 2018: Public disclosure.
Researchers
- Nick McClendon
- Andrew Mirghassemi
- INIT_6
- Chris